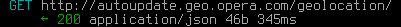 which includes your country and the precise timestamp.
which includes your country and the precise timestamp.
A web browser made by Opera Software, using the Blink engine. Has some interesting features like mouse gestures, a built-in ad blocker and VPN. It is the sixth most popular browser. But how does it look like in terms of privacy?
Opera makes 55 unsolicited requests upon its first run. By default, it spies on all your browsing history. Works closely with advertisers and trackers. Is integrated with Facebook, one of the biggest privacy violators in the world. Has Google as the default search engine. Closed source.
The first request Opera makes is the geolocation request: 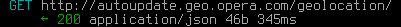 which includes your country and the precise timestamp.
which includes your country and the precise timestamp.
If this is the first time you run Opera, it makes this request:  which will redirect you to their homepage. Then, that homepage will make a bunch of other requests, including to google analytics, facebook (if you're logged in, they now know who you are), and even yandex.ru. The yandex request will set a uniquely identifying cookie.
which will redirect you to their homepage. Then, that homepage will make a bunch of other requests, including to google analytics, facebook (if you're logged in, they now know who you are), and even yandex.ru. The yandex request will set a uniquely identifying cookie.
Later, it will make a few requests to cxense.com. What is Cxense?
We are Cxense. We help hundreds of leading publishers and marketers across the globe transform their raw data into their most valuable resource. Built on the premise of 1:1 analytics and communication; allowing you to both gain unprecedented insight about your individual customers, and to action this insight real-time in all your marketing and sales channels.
This request seems to include a unique ID
Opera will also download a list of search engines, which you cannot delete, only add new ones (at least from the GUI). Apparently, there are some convoluted methods of deleting the search engines, but I haven't confirmed them.  Of course, the default search engine is the anti-privacy Google.
Of course, the default search engine is the anti-privacy Google.
Opera will query OCSP servers (ocsp.comodoca.com) to check if SSL certificates expired.
Anytime you visit a website, Opera will make a request like this: 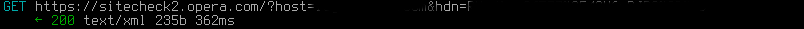 to check if it is malicious. So it is literally spying on your whole browsing history. Fortunately, this can be turned off.
to check if it is malicious. So it is literally spying on your whole browsing history. Fortunately, this can be turned off.
Other requests include ones to googletagmanager, google ads specific for your country, more requests to yandex (these include your screen size, encoding, and the page you came from), more geolocation, etc. Together, Opera made 55 unsolicited requests in my first run of it. Analyzing them all would probably take a book.
Opera has a Facebook chat button on the sidebar, and Facebook is one of the most anti-privacy organizations out there.
Opera has a list of "partners" — those are the websites that are in the Speed Dial by default. If you click on one of them from there, they will know you visited from Opera's Speed Dial. Those requests also include unique user IDs. What happens if you close Opera and run it again? The websites in the Speed Dial will change to the ones from your country! And the same rule about them knowing where you came from applies.
And it will stay that way. From their FAQ (the message used to be there in 2017, they must have deleted it somewhere in 2018):
Opera has no current plans to open source its browser.
Therefore, some other spyware might be hiding in there.
This article was written by digdeeper.neocities.org
Formatting changes were done by the site maintainer.
This article was last edited on 6/8/2018
This article was created on 11/25/2017
If you want to edit this article, or contribute your own article(s), visit us at the git repo on Codeberg. All contributions must be licensed under the CC0 license to be accepted.
